BECE 2024 - INFORMATION AND COMMNICATION TECHNOLOGY (ICT) II
THEORY QUESTIONS
This paper is in two sections: A and B. Answer Question 1 in Section A and any other three questions in Section B.
Answer all the questions in the space provided in this question paper. At the end of the examination, you should submit the entire question paper to the invigilator.
Any candidate who tears off any part of the question paper will be severely penalized.
Whether you answer all the questions in this paper or not, hand in the entire question paper to the invigilator.
Credit will be given for clarity of expression and orderly presentation of material.
SECTION A
Answer Question 1
[Compulsory]
1. Figure 1 shows computer users in a school's computer laboratory.
Study the figure carefully and use it to answer questions 1(a) to 1(g).
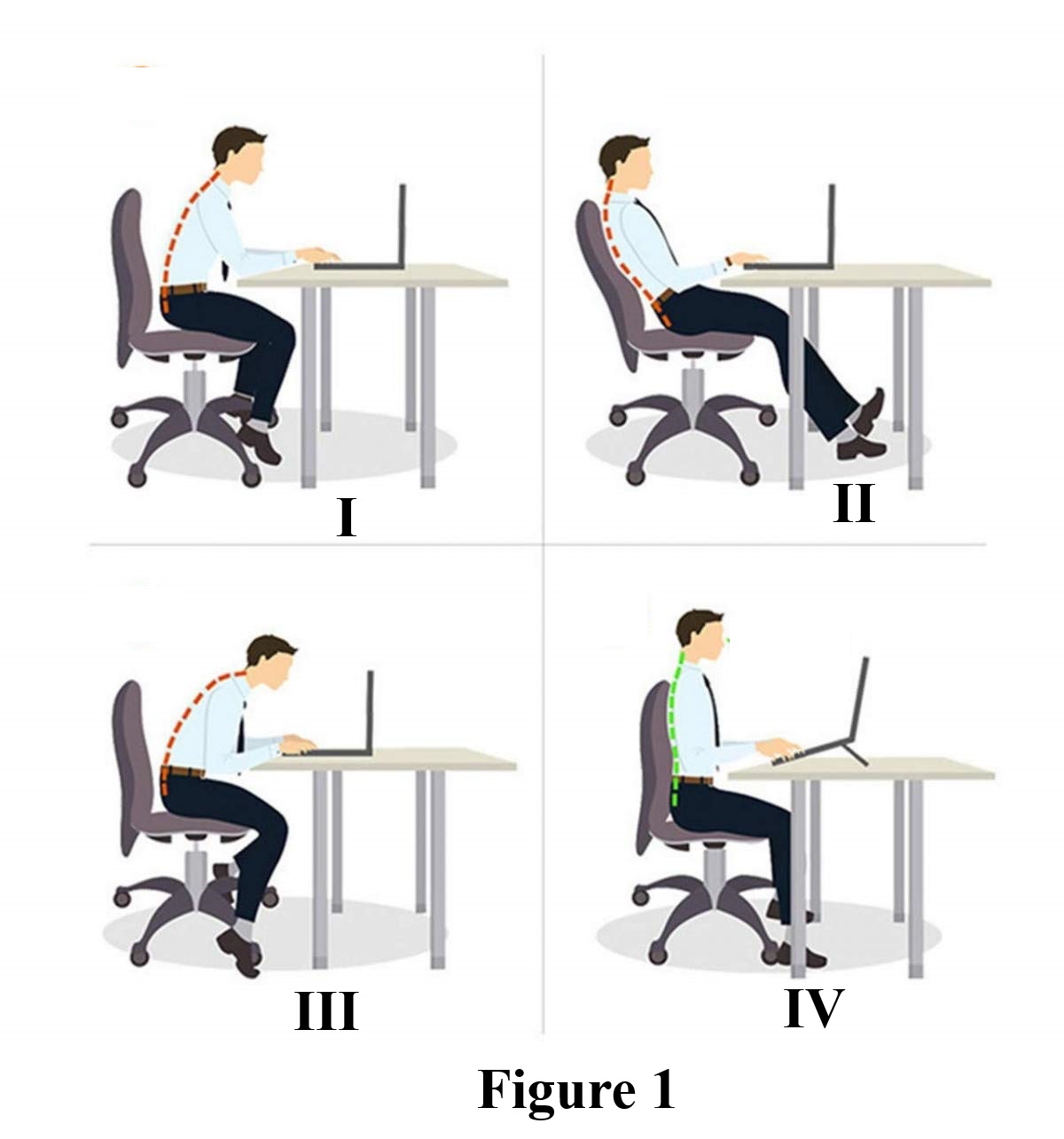
(a) Which of the users has assumed the correct posture?
(b) Prolonged use of the computer is associated with health-related problems.
Suggest two possible safety measures the users should adopt to minimize workstation risks.
(c) The users were tasked to produce a ten-page document using Microsoft Word. Outline the steps to be taken by the users to set the entire ten-page document to 2.0 line spacing.
(d) The users were to type a report using Microsoft Word to be presented in class. User I typed 10 pages within 3 hours, user II typed 8 pages within 4 hours, user III typed 5 pages within 6 hours and user IV typed 6 pages within 2 hours.
Suggest two Microsoft Excel chart types that will be most appropriate to show the relationship between the number of pages each user typed and the time spent in typing.
(e) The users have been using their computers as standalone.
State two benefits they will derive when their computers are networked.
(f) As a networking consultant, suggest two network topologies that could be used to network the computers for the users.
(g) The following activities were given to each user to type using Microsoft Word. They were to use Microsoft Publisher to produce a flyer with the typed document to be displayed on the notice board of each classroom.
School routine activities
7:30 a.m. : Morning assembly
7:40 a.m. : Classes hours
9:40 a.m. : Morning break
10.00 a.m.: Classes hours
12:30 p.m. : Afternoon break
1.00 p.m. : Classes hours
2:30 p.m. : Closing
As a programming student, write an algorithm to demonstrate the activity.
SECTION B
Answer three questions only from this section
2. (a) Describe the processor of a computer to colleagues in your class.
Study Figure 2 carefully and use it to answer questions (b) and (c)

(b) Write the name of the image shown in Figure 2.
(c) Describe to your colleagues, how the image shown in Figure 2 is accessed for information.
(d) File extension is very important in naming a file. List three file extensions to be presented in the next computing class.
3. (a) The head teacher of ABC JHS bought the following items for school. 10 footballs for GH₵ 2,000.00, 20 notebooks for GH₵ 400.00, 50 pens for GH₵ 250.00, 8 registers for GH₵ 240.00 and 2 laptop computers for GH₵ 7,000.00.
(i) How many columns and rows are needed to create a table for the head teacher’s items bought including ABC JHS as heading for the table without the serial numbers of the items?
(ii) Outline the steps to be followed to create the table mentioned in 3(a)(i) using Microsoft Word.
(b) The file size of a presentation created by a student is too large to be sent through e-mail to a friend.
Suggest one possible reason for the large file size.
(c) State one feature of Microsoft Publisher.
(d) Study the Microsoft Excel worksheet carefully and use it to answer the question that follows.
| A | B | C | D | E | |
| 1 | NAME OF STUDENT | TERM 1 | TERM 2 | TERM 3 | TOTAL |
| 2 | Kofi Malik | 84 | 75 | 88 | 247 |
| 3 | Ama Ghana | 85 | 74 | 86 | 245 |
Write a function in Microsoft Excel to determine the lowest termly score for Kofi Malik.
4. (a) Computer networks come in several topologies.
State two features of the ring topologies.
(b) Abu, the leader of a class does not understand how to use the Forward all feature in an e-mail to send a message to everyone in the class.
Explain to Abu what Forward all means.
(c) A computing teacher has given a class an assignment to design a personal blog.
(i) What two design features should be used to design the blog?
(ii) Write the name of one tool that can be used to design the blog.
5. (a) In computer operation, expressions are evaluated using operator precedence approach. Follow the approach and evaluate the expression:
(1+3)*5+7
(b) How would you describe the term decomposition in programming to a friend who was not in class when it was taught?
(c) Mention three software packages that are used in the construction of robotic artifacts.
(d) Write a possible IF-THEN statement for an imaginary expert system to execute the statement:
You are a Monday born and a female which means you are called Adwoa.


 TeacherDora Admin
TeacherDora Admin